When it comes to personal data the key element is whether we can link data in question to the person. There are many legal, technical and logical nuances regarding to concluding if the person is identifiable or not. But the bottom line is that data privacy is about the consequences to that person.
Not all consequences are equal – some may seem rather trivial, whilst in edge cases the some threats may materialize with irreversible impact to the person (e.g. health and quality of life). As threats evolve and new technologies also become available (and sometimes new tech also brings along new threats). Think of blockchain and advances in the field of cryptography but also privacy enhancing apps and digital tools that are increasingly accessible for a wider audience (from self-made VPN to privacy friendly operations systems like Qubes OS (https://twitter.com/QubesOS)).
Countries currently focus on the regulations that establish the obligation to implement privacy principles and propose a sanction if them principles are not implemented. However there does not seem to be much consideration whether and how could a country implement some principles on a systematic level that would boost the level of privacy for the whole nations.
Enter ‘privacy by design’. Who gives an identity to a person? The State. Who imposes rules and processes of identity provision? The State. Therefore, it seems only logical, that a country itself should also be concerned whether its identity provision is on par with the regulations.
The official identity of a person is given or assigned by the State. The process may vary in details in specific countries, but every country has some say in how identities are given. At least we can’t think of a country that is not interested in connecting rights and obligations available in the country to an “identity management” not controlled by the country itself. In other words, every countries actions regarding registering and creating identities for people could be considered as a giant ‘Identity and Access Management’ (IAM) scheme, where the access to rights and obligations are directly linked to the legal identity provided by the state.
The baseline official identity consists of a human readable elements, such as an official name and an unique identifier (social security code or some sort of personal code, usually consisting of numbers). In some cases, the unique identifier might be substituted with date and location of birth, but these are rather rare occasions and specific exceptions which do not affect the system as a whole.
We use our name and the unique identifier for public and private services all the time. Yes, sometimes a correct VPN solution can boost privacy, but from the point of view of a financial service provider or an authority entity (such as the IRS), the person is always identifiable based on the sole official identity.
Since start of the birth, different government and public entities use the data to provide services but also to create new records related to name and the personal code (from medicine and education to obtaining licenses, registering for voting etc). Private entities do the same – from insurance and banking to a simple sign-up for a customer loyalty program. All that is creating new personal data, linked directly to a person’s official identity.
But remaining anonymous is not the purpose of ‘privacy by design’. From privacy point of view, the question is, do all these government and private entities really need to know our official identity which all types of different data can be linked to? Privacy engineer would ask that if the public IAM would allow pseudonymous ID-s from the start, would it change any thing for the public and private entities? Probably not(hing).. But would it change anything for the person? Yes – this would mitigate many threats and lower the probability of many more. And it would still be possible to use services, enable being KYC-d by your bank etc.
The reasoning is that whilst not anonymous, pseudonymous layer could be provided by the system for cases where the public or private entity does not actually need to know your name and personal code. Even if it is necessary to ensure that the person would still be legally responsible and consequences can be delivered (i.e fulfilling court decisions etc), there are still many levels of pseudonymous IDs that could be protect individual’s privacy whilst the operations of public and private entities remaining unaffected.
The state is already the single source of truth regarding how the person is linked to its official ID. The state could remain the single source of truth, while also providing ensuring privacy for persons and perhaps even facilitating data exchange protocols that would benefit the private and the public sector.
Example: The person is given and official ID (name and a personal code) – John Smith, AB123456789. The person is also given pseudonym ID’s which could be human readable or in some cases only machine readable formats (think of IP addresses and how ‘computers’ find the right website). For simplicity – say the state creates two layers of pseudonyms for John – Pseudonym #1- ‘ABCD’ and pseudonym #2 -‘JS1234’. From now on, the state entities could link it’s records with the ‘ABCD’. Private entities such as banks could rely on ‘JS1234’ and not really know that it’s linked to John. If there is a need to create legal consequences, it is backed by the state who has the key to link ‘JS1234’ to John Smith, AB123456789.
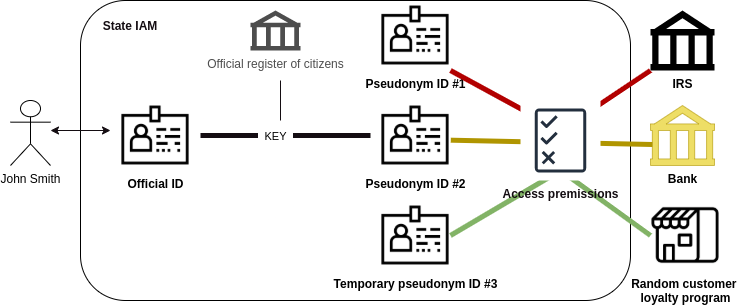
In case of a data breach, all that is disclosed is the data regarding ‘ABCD’. Another data breach might disclose data related to ‘JS1234’. As long as the key that links the pseudonyms to the original official identity, the breaches will have minimal impact to John. The extra level of privacy also mitigates risks where entities legally or illegally gather troves of personal data and ‘enrich’ it data or create profile with such data. Furthermore, official pseudonymous ID-s could enable people to use ‘one-time ID’s’ (think of virtual credit cards that can be created and closed as needed).
Summary. In a high level logical assessment, it seems possible that people would still receive services and bare consequences based on an official pseudonymous ID. Sure, there would be many obstacles for implementing such design, but this would also create opportunities, many of we can think of at the moment.
If you want to implement ‘privacy design’ for your future or current business, cont(r)act us for privacy engineering.
